If an engineer ends up leaving a company, on their own, or for any other reason, the company work is going to have to quickly work to change all of their keys for their credentials and keys application components.
That’s a huge hassle, because often times it’s hard to know where they are stored, who can access what, and how to change everything at a massive scale — especially if the company is a huge one. Dane Schneider hopes to change that with a new service called EnvKey, a way to create a kind of encrypted repository internally where a company can store all its API credentials in order to make them easy to update, as well as manage who has access to what. Think of it as a sort of LastPass or 1Password, but for important credentials within a company. EnvKey is launching out of Y Combinator’s Winter 2018 class.
“At the last place I worked, a coworker got fired and my manager said he said, okay, we need to change all the API keys across the infrastructure — and it was Friday at 4 p.m.,” Schneider said. “I had to tell him that’s not something we can just do right now. That’s a bit of an undertaking. I had been thinking along those lines, I had the idea in my mind, then I thought man if we had something that we could just update this in one place it’d be really simpler. We’d be able to deal with the security issue going right now. We would share [our keys] over email or Slack, but it always felt like the wrong thing to do security-wise.”
Schneider is a solo-founder in Y Combinator, which is a bit of an anomaly, but the idea sounded smart enough given that it’s a pretty big issue among companies — especially as they scale. Engineers might run into the problem where they accidentally publish their credentials on Github while updating a code repository, which could lead to potential security issues for that application. The hope is this offers startups and companies an opportunity to not only make those keys easy to manage and update, but also locked up tight to make sure something like that doesn’t happen in the first place.
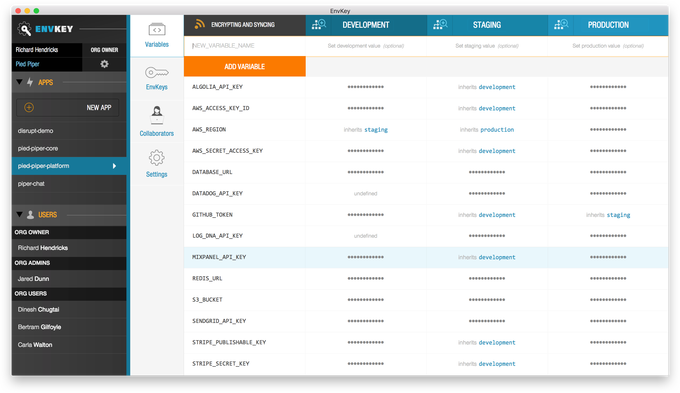
Each company has its own account, with a user interface where a company can start entering configuration information for their applications. They can also import from another system, and then invite the rest of a team through email and generate keys that Schneider calls EnvKeys. Users can create a developer level access key, for example, and then set it in a env file like one in a python project — which will always have access to the latest credentials every time someone runs that project. When an app runs, it’ll grab the latest configuration, decrypt it, and synchronize it. There are simple access levels, where someone can access it for development and staging, or servers, or administrators that can invite additional people.
EnvKey stores the API keys, which are end-to-end encrypted, and Schneider says the company doesn’t have access to the information. The hope is that companies will upload that information and feel good about it being stored securely and that they can quickly update and shift around credential information as necessary. Schneider also wants to build EnvKey to work on any platform, rather than having it pinned down to a single one, such as one Amazon might do for its web services for example.
There is going to be plenty of competition for this kind of low-hanging fruit for managing this information, given that it can lead to massive headaches for companies. Already there are startups like Hashicorp, which raised $40 million in October last year, and of course the major infrastructure providers may look to build something similar in their own ecosystems. But Schneider’s hope is that EnvKey can have a simpler approach and work in most environments, which can help convince engineers — especially as the companies grow up — to start using it.
“[Products like Hashicorp’s vault] take a pretty high level of developer operations expertise to set up and run it,” Schneider said. “Unless you’re prepared to do a pretty substantial project, it’s pretty tough to work with. Another is AWS has a service called parameter store, which can work pretty well if you’re again, pretty savvy, with AWS and you’re using AWS services for everything else. That makes sense, but it also comes along with the complexity and baggage AWS has in general. There’s a lot of things to configure. There’s a pretty high learning curve with that.”