When Equifax was broken into late last year — one of the biggest security breaches in recent history — Fletcher Heisler wanted to make sure security engineers got to know exactly what happened right away, and how to fix it.
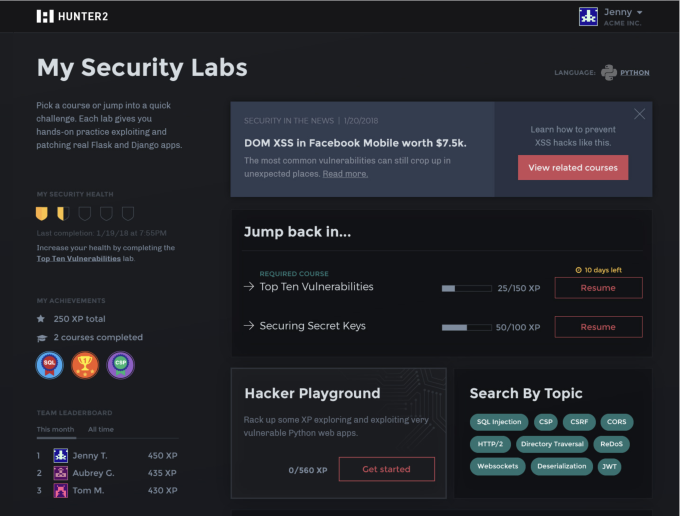
That’s part of the goal of Hunter2, a new online learning platform for security engineers that’s designed to teach them how to handle these kinds of breaches in a more hands-on way. Hunter2 aims to spin up training labs centered around real-world scenarios to teach engineers exactly why something broke in a web app, and how to fix it. Engineers work through responsive web apps, which are spun up on a fully functional server, that include some scenarios built off of real-world events — like the Equifax hack. It’s essentially like a game, where they try to break it and fix it, except it isn’t happening quite in the real world. Hunter2 is launching out of Y Combinator’s winter 2018 class.
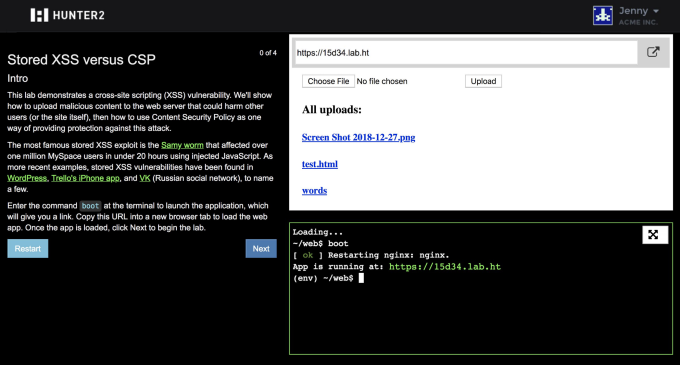
“We try to keep every lesson in the context of what’s happening in the industry and what’s happening in the wild,” Heisler said. “We spin up a lab in 20 minutes that perfectly replicates the vulnerability. Engineers can get hands on practice. We train them — here’s what happens, here’s what they should have done, here are the best practices that should have been followed and gonna patch the code. It’s one thing to teach a topic in the abstract and say, beware of SQL injection, it’s another to tie this to something that’s happened.”
Hunter2 was in some ways born as a response to training programs for engineers within companies where they check in for a few hours every year to ensure that they are somewhat up-to-date with the current security environment on the Web. But as development languages continue to evolve rapidly and new frameworks like NodeJS become more and more popular, these programs are sometimes finding themselves in catch-up mode, Heisler said. That, and the approach needs to be more hands-on, rather than just a typical video class.
Engineers then go through a number of challenges to identify their strengths and weaknesses. If they run into problems, they go more in depth into the skills where they need some work. Think of it like the sorts of compliance training you might need for larger organizations, except it’s a routine check-in on making sure you know all the right skills in order to deal with issues as they arise.
There are plenty of industries that need to be more conscious about security, like healthcare for example, and need to make sure their engineers are trained and ready for new scenarios as they emerge. Hunter2 aims to be a sort of ramp-up for joining those companies, and one an engineer will check back in for a couple of hours every month to make sure they’re still working those muscles, so to speak. Companies can customize the content they are seeing with their own kinds of vulnerabilities, and Hunter2 helps create content for them for their engineers to work through.
“[We have a problem with] traditional training because it’s based in slide decks and videos is a lot harder to update,” Heisler said. “It takes a lot of time to keep up to date with new tech. Its not like were gonna miraculously create half a million cyber security experts in the next year or two. What we can do is teach those basic skills to a number of people who are becoming not just developers but tech workers in general. That’ll become a much more fundamental piece of every role in the next couple years. That way we can save a lot of time and money upfront by giving those security skills to the right people working in tech or getting into tech but bringing the right mindsets.”
That idea of teaching in a simulated or more hands-on environment is an area that’s gathering more and more interest. If you look at sites like Codecademy, there are some places that are trying to focus on the do rather than the watch in order to teach people how to code and start dealing with more real-world scenarios.
After all, if you’re in the process of learning how to program, one of the pieces of advice people will give you is probably “go work on a project” — and that kind of freezing up to figure out what kind of a project can be a big barrier to entry to learn how to apply those skills. Hunter2 aims to build its own virtual environment to handle these kinds of scenarios, rather than just simulations, in order to offer its own flavor of how to teach how to handle these problems.
“You don’t actually have the full control over your access what we’ve done is put lessons on the left and a server on the right,” Heisler said. “There are a couple similar platforms but they sill simulate access. The difference is there’s time for hands on keyboard training. Having time to exploit or patch seems to be the right way to teach the lessons hand on. I think a lot of security education coming from traditional security is coming from the fact or academic spaces that.”
Featured Image: Krisztian Bocsi/Bloomberg/Getty Images